- Have any questions?
- +91 9176206235
- info@phdsupport.org
PhD in Network Data Security of UAV vehicles

PhD in cyber security UAV based password cracking attack
May 14, 2021
PhD in Congestion Control in WSN
May 16, 2021Proposed Data Security Mechanism:
This work has presented a security mechanism for detecting compromised UAVs in UAV networks for supporting surveillance. It is based on the assumption that people will be usually observed in the border by more than one UAV. Hence, if a UAV repeatedly reports people that are also reported by other UAVs, each UAV will detect this fact following an information diffusion approach inspired by the principles of blockchain. We developed the novel simulator called Opportunistic Network simulator to illustrate this approach. The experimental results indicated that Data Security in Networks of unmanned aerial vehicles real world UAVs. In particular, we plan to apply this approach in the surveillance of country border for detecting cross border activities and reporting. This work may also be tested for assisting military operations in detecting possible threats in critical borders where the terrain is difficult to monitor for military movement.
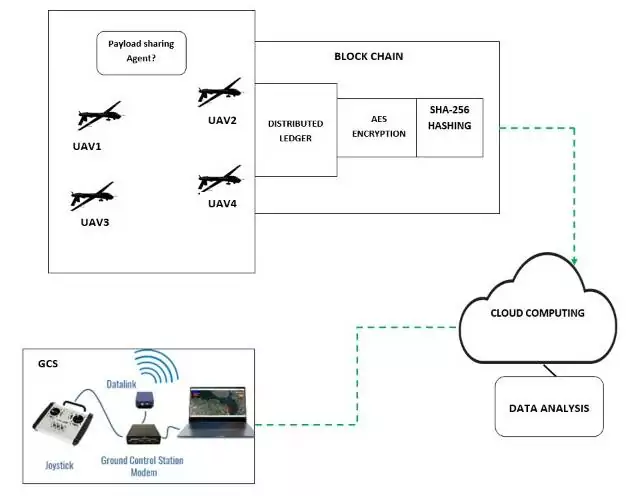
Blockchain Distributed Ledger :
Wireless UAV Network allowed UAV vehicle to vehicle communication which truly imitated by the distributed blockchain methodology which identifies misbehavior UAV’s against trust policies. The blockchain based secure asymmetric encryption occupies the UAV’s network broadcast list. The proposed methodology is finally captured the malicious UAV or detected the hijacking UAV.
PhD support provides paper writing and coding implementation for PhD in Data Security in Networks of unmanned aerial vehicles.
Trust Policy :
Wireless UAV Network allowed UAV vehicle to vehicle communication which truly imitated by the distributed blockchain methodology which identifies misbehavior UAV’s against trust policies. The blockchain based secure asymmetric encryption occupies the UAV’s network broadcast list. The proposed methodology is finally captured the malicious UAV or detected the hijacking UAV.
PhD support provides paper writing and coding implementation for PhD in Data Security in Networks of unmanned aerial vehicles.


