- Have any questions?
- +91 9176206235
- info@phdsupport.org
PhD in Fake Packet Injection Attack in UAV Vehicles

PhD in Blockchain Based Cyber Security
May 25, 2021
PhD in Routing Low Power & Lossy Networks Protocol
May 26, 2021PhD in Fake Packet Injection Attack in UAV Vehicles
INTRODUCTION
Unmanned Aerial Vehicles or UAVs are aircraft that are flown in absence of a human being, typically controlled by a remote. These are infused with vulnerable monolithic software and have raised some serious concerns in the recent past as they are subjected to security attacks. Their components are usually networked and as they are operated in the real world, ample problems are witnessed with the current technology and hence a proposal is made through this research paper that can build a practical software system robust to cyber attacks.
PhD in Fake packet injection attack in UAV vehicles
IDEAS
The aim is to propose a new model of UAV that is capable of discovering, notifying, and terminating security vulnerabilities associated with the functioning of UAFs in the real world.
PhD in Fake Packet Injection Attack in UAV Vehicles
ISSUES IN THE CURRENT TECHNOLOGY
The current technology embedded in the construction and functioning of UAVs has made them vulnerable to cyber-attacks. Secondly, there is a need for a technology that can be used to verify the correctness of digital circuits, security, and communication protocols.
APPROACH
The method of fake packing injection attack will be implemented in the proposed model. This model is based on the combination of fuzzing and Bounded Model Checking or BMC technology to determine and terminate the vulnerabilities leading to cyber attacking. This will be done by detecting various security vulnerable factors. The International Software Verification Competition, SV-COMP, was run on Linux OS with 15 GB RAM for 15 minutes.
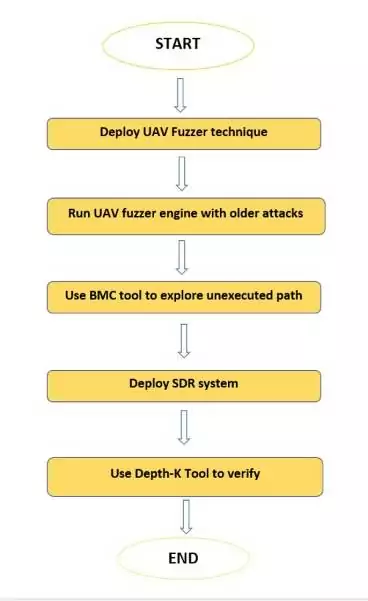
PROPOSAL
In this proposal, a preliminary verification approach called “UAV Fuzzer” is deployed to detect the vulnerabilities leading to cyber-attacks. To begin with, a fuzzer engine was run by incorporating the test cases that were stacked in the past. In particular, the research model was focused on vulnerabilities like no buffer overflow, no dereferencing of null pointers, and no pointers pointing to unallocated memory regions.
The BMC tool functions opposing the target software so as to explore its uncovered state-space. Here the aim was to determine the unexplored execution paths of the UAV software.
Going forward, the technology of Software-Defined Radio or SDR System was used to receive, transmit and analyze the operational connection system of the Unmanned Aerial Vehicles. This proposed model is also based on the evaluation of the DepthK tool over some benchmarks to verify and falsify safety properties in C programs using the BMC and k-induction rule.
Our Experts Provide complete guidance for PhD in Fake packet injection attack in UAV vehicles. PhD in Fake packet injection attack in UAV vehicles Coding and implementation support.


