- Have any questions?
- +91 9176206235
- info@phdsupport.org
PhD in cyber security UAV based password cracking attack

PhD in Blockchain-SDN based IOV system in 5G Network
May 14, 2021
PhD in Network Data Security of UAV vehicles
May 15, 2021UAV based Password Cracking cyber attack has no privacy, data confidentiality, integrity and availability. The authentication based security system is highly trusted for communication between two drones. Also non cryptographic lightweight IDS and cryptographic based strong periodic passwords and strong encryption algorithm is highly suggested for UAV data privacy.
In the uncertain environment, drones are predominantly used to target guest Wi-Fi connections, Bluetooth and real time drone devices. The instant Bluetooth connections are not protected and not measured any security alignments, which recognize that no one UAV application could get close enough to compromise them for internal network data access in wireless signals. This lead to weak single factor password authentication and the utilization of the network access password that could be easily cracked by the attacker.
PhD Support providing PhD in cyber security UAV based password cracking attack , paper writing and coding implementation.
The advanced three-Way Handshake method is processed with multiple devices. This handshake process is based on UAV network router’s AP and the UAV network newly integrated rogue device. The malicious behavior of the attacker starts de authenticates the attacker and collapse the network traffic communication among the drones. Finally handshake method can be used in order to launch a duplicate password cracking attack, especially if the UAV network drone is secure.
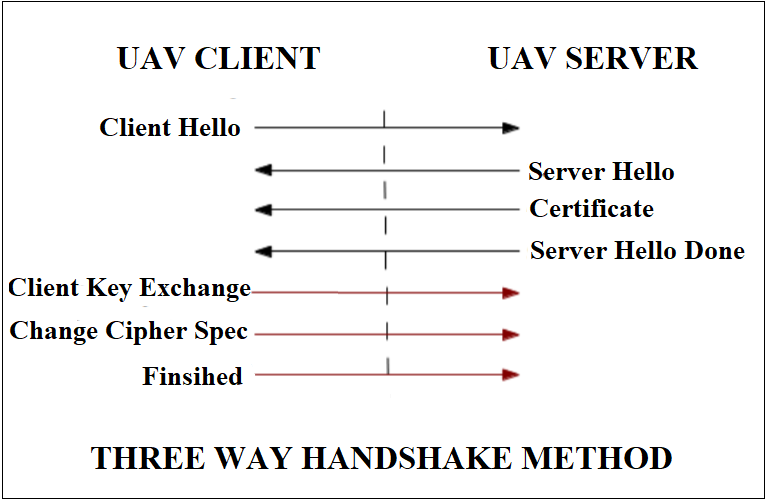
The real time industrial application performed a cyber attack against ,how to take entire control over a UAV Network, and produced some security vulnerabilities in real time industrial application UAVs. In the UAV based cyber attack take advantage of weaknesses in the communication system to communicate to the UAV device .The application oriented UAV drone is enabled with Wifi network. The malicious system uses the Wi-Fi using a password cracking tool called Air cracking, which degrade the user authentication and provides access to the attacker. After taking complete control over the UAV network vehicle they created data access in real time applications with simple drone devices. Cracking passwords to get data access to a UAV system is a violation of Data Authentication and which could be categorized as Spoofing Identity.
PhD Support providing PhD in cyber security UAV based password cracking attack, paper writing and coding implementation.
We are providing real time coding implementation for PhD in cyber security UAV based password cracking attack.


