- Have any questions?
- +91 9176206235
- info@phdsupport.org
PhD in Cyber security threats against UAV System

PhD in Cryptography using Elliptic Curves
May 16, 2021
Ph.D paper writing in Artificial Intelligence Research Topics
May 25, 2021PhD in Cyber security threats against UAV System
INTRODUCTION
Wifi-based UAVs are prone to cyber-attacks and due to their widespread usage in various commercial and defense fields, there is a need for a technology that can protect them against getting exploit.
This research paper is based on a comprehensive security framework that deploys a defense-in-depth approach so that it can minimize the vulnerability of cyber security attacks and data breaching.
PhD in Cyber security threats against UAV System
IDEAS
Many large-scale organizations are planning to deploy Unmanned Aerial Vehicles so as to minimize the manpower and maximize consistency, accuracy, and speed of delivery. The proposed model intends to mitigate the chances of cyber security threats in this technology.
ISSUES IN THE CURRENT TECHNOLOGY
In the current technology, the hackers are able to exploit open Telnet access and issue a de-authentication attack that forces the Parrot AR and Bebop UAVs.
APPROACH
The proposed research paper is based on a new Bebop Platform. A watchdog timer has been added to limit the time period (t) taken by the CPU for non-navigational processes. It is deployed to safeguard the DoS attacks and will operate in the domain of the OS. A hardline input data filtering of all the data is directed to be sent to the UAV’s embedded system as it will be capable of interrupting and terminating the non-compliant process. Also, the anti-spoofing mechanism will mitigate the entire structure against malicious cyber-attacks.
The proposed model is based on three common attacks; Denial of Service or DoS, Buffer-overflow, and ARP cache poisoning. This will be supported by a multi-layered framework against cyber-attacks this is extendable and could be easily implied to defend attacks against other threats.
PROPOSAL
In the proposed model, penetration testing was performed on the UAV and developed exploits that enabled to conduct of DoS, buffer-overflow, and ARP cache poisoning attacks against it. The Parrot Bebop is a P7 dual-core CPU with a quad-core GPU.
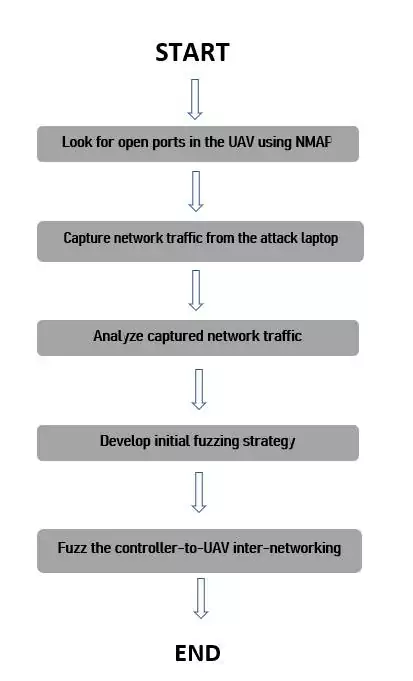
Firstly, the open ports are to be looked at in the embedded system of the Unmanned Aerial Vehicle by deploying NMAP. Then, the UAV is to be made to take a flight and network traffic from the attack laptop has to be monitored well.
The captured network has to be analyzed so as to develop an appropriate fuzzing strategy. Lastly, fuzzed the controller-to-UAV inter-networking and the captured network can be sent up to 1000 JSON.
Our experts provide complete guidance for PhD in Cyber security threats against UAV System.
PhD in Cyber security threats against UAV System, coding implementation support.


