- Have any questions?
- +91 9176206235
- info@phdsupport.org
PhD in Cyber-Attack Detection and Mitigation

PhD in WSN Data Dissemination Using Machine Learning.
May 26, 2021
Phd in Security Attacks & Energy In WSN Network
May 27, 2021PhD in Cyber-Attack Detection and Mitigation
Data is the most treasured thing of IoT as researchers are reliable on enormous datasets that help them to analyze and draw solutions. As the Science of Security (SoS) is emerging, cyber detection and mitigation are expected to go more data-driven. Currently, these cyber attacks are sought post facto by forensic analysis.
Data is extremely important for inducing, validating, and refuting SoS based theories, and for that, it is crucial for the data to be accurate and reliable. This demands for advanced techniques and technology that completely secure the data transmission process.
Idea
The idea is to develop a framework that can detect the vulnerabilities that lead to cyber attacks. This can be done by creating a model that interacts between the different factors such as the adversary and the system defender.
Issues in the existing technology
In the existing technology cyber attacks occur frequently. Due to several heterogeneous components like diverse computing systems and various types of networks the existing technology has become quite complex. Detecting and mitigating cyber attacks in the complex structure is more challenging.
Approach
In the proposed research, context representation and sharing have been done by developing components and agents that share a common ontology and communication language. To detect the attacks, we applied the technique of combining description logic and rule based logical inference that is both feasible and scalable.
This approach can lead to inconsistency and to overcome that the research proposal has been drawn on a range of general approaches like assumption based abductive reasoning, modeling, and augmentation protocols.
Proposal
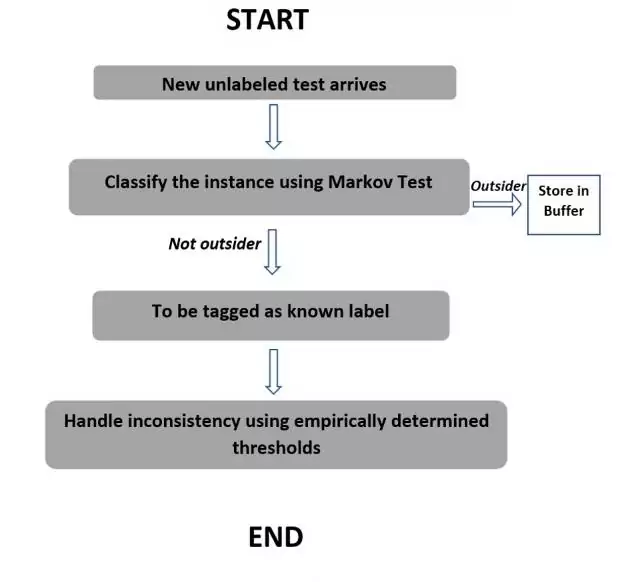
In the proposed model, we assume that the data stream is divided into equal-sized chunks. On arrival of a new unlabeled test, the ensemble will be used to classify the instance. If it is detected as an outsider, it will get stored in the buffer so that it can be studied further. If this is not an outsider, then it will be tagged as a known label. The buffer will be examined frequently after fixed intervals to determine the arrival of the novel class. If so, then the instances belonging to the novel class will be identified and tagged accordingly.
Then Markov network has to be used for collective classification over several sources of the data received.
Our Experts Provide complete guidance for PhD in Cyber-attack detection and mitigation. PhD in Cyber-attack detection and mitigation coding and implementation support.


