- Have any questions?
- +91 9176206235
- info@phdsupport.org
PhD in Man in Middle Attack Against UAV Systems

PhD in Dos Attack Against UAV Communication System
May 27, 2021
PhD in Packet Spoofing Attack Against UAV System
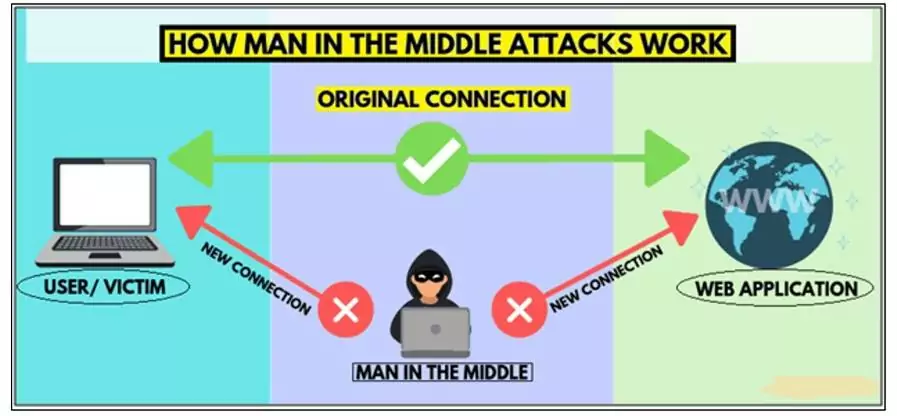
May 27, 2021PhD in Man in Middle Attack Against UAV Systems
The development of the internet of Drones (IoD) becomes vital because of implementing drone-based civilian or military resources. The drones are open-source connectivity networks which need high secured connectivity for the wireless networks. Now, these drones are used in many resources however still there is a thread in the security aspect. Thus control framework is assigned to incorporate security into an automatic design which establishes a cyber-physical signal to updating the cyber defense and physical layer control decisions based on Man in the middle attack against UAV systems
RESEARCH APPROACH:
The leakage of such information can lead to a big loss in terms of piracy and data leakage. Threads are also needed to consider as an exploiting vulnerability by introducing certain IODs. The real-time capturing and processing of dataneeds a lot of energy and memory where dynamic load balancing in IoD can be considered as an effective solution. This behavior can be an indicator thatthe UAV has been hijacked and the attack translates to investing less energy in the assigned task. The Man in the middle attack against UAV systems comparative approach enables the audit difference between abnormal behaviors due to the cyber-physical attack .thus the proposal is the observations on Man in the middle attack against UAV systems
LATEST ISSUE:
- Sometimes UAVs are not able to complete their task due to certain environmental and technical issues.
- Facing the hardest environmental condition also leads to consume energy and causes deviation from its expected path.
- The protection against physical attack is needs to consider issue in IoD devices due to its expense.
- Over heading of IoD in energy and delay leads to various issues like resource degradation and low efficiency.
PROPOSED SOLUTION:
- By using an Online trust monitoring mechanism that the central unit regularly observes the operation of UAV in terms of energy consumption as well as performing the assigned task.
- It gives the UAVs a certain time to recover from the potential technical issues if they may face during task completion.
- The low-cost solution needs to develop for enhancing the utilities of IoD for effective communication in UAVs.
- Time strategies and easily updateable solutions are required to attack the various unknown cyber attacks
FUTURE PROPOSAL:
- In this proposal Man in the middle attack against UAV systems Recursive least squares (RLS) is applied to perform estimate and tracking of the controller parameter
- Rather than relying on self-report of the UAV to declare the number of their completed task as the future development based on this previous observations.
Our Experts provide complete guidance for PhD in Man in middle attack against UAV systems.


